We've all seen the headlines: "5-Year-Old Industrial Controller Hijacked in Botnet Attack" or "Medical Device Recalled Due to Cybersecurity Vulnerabilities." While hardware gets the initial attention, the real challenge in embedded systems isn't the silicon—it's ensuring your software remains secure, compatible, and maintainable for a device that might be in the field for 10-15 years.
The harsh reality? Your carefully selected processor will likely be obsolete long before your product reaches end-of-life. The true test of embedded engineering isn't just making it work today, but maintaining it securely for the next decade.
The Three Pillars of Embedded Software Longevity
1. Strategic Kernel Management: The Foundation
Choosing and maintaining your Linux kernel is the most critical decision for long-term viability.
The LTS (Long-Term Support) Imperative
Stick to established LTS kernels (5.15, 6.1, 6.6) that receive backported security fixes
Avoid the temptation of mainline kernels for production devices
Plan for regular, scheduled kernel upgrades (every 2-3 years) rather than emergency patches
Real-World Example: A medical device manufacturer using kernel 4.19 faced a critical vulnerability. Their upgrade to 6.1 took 6 months of testing—time they wouldn't have had if the vulnerability was being actively exploited.
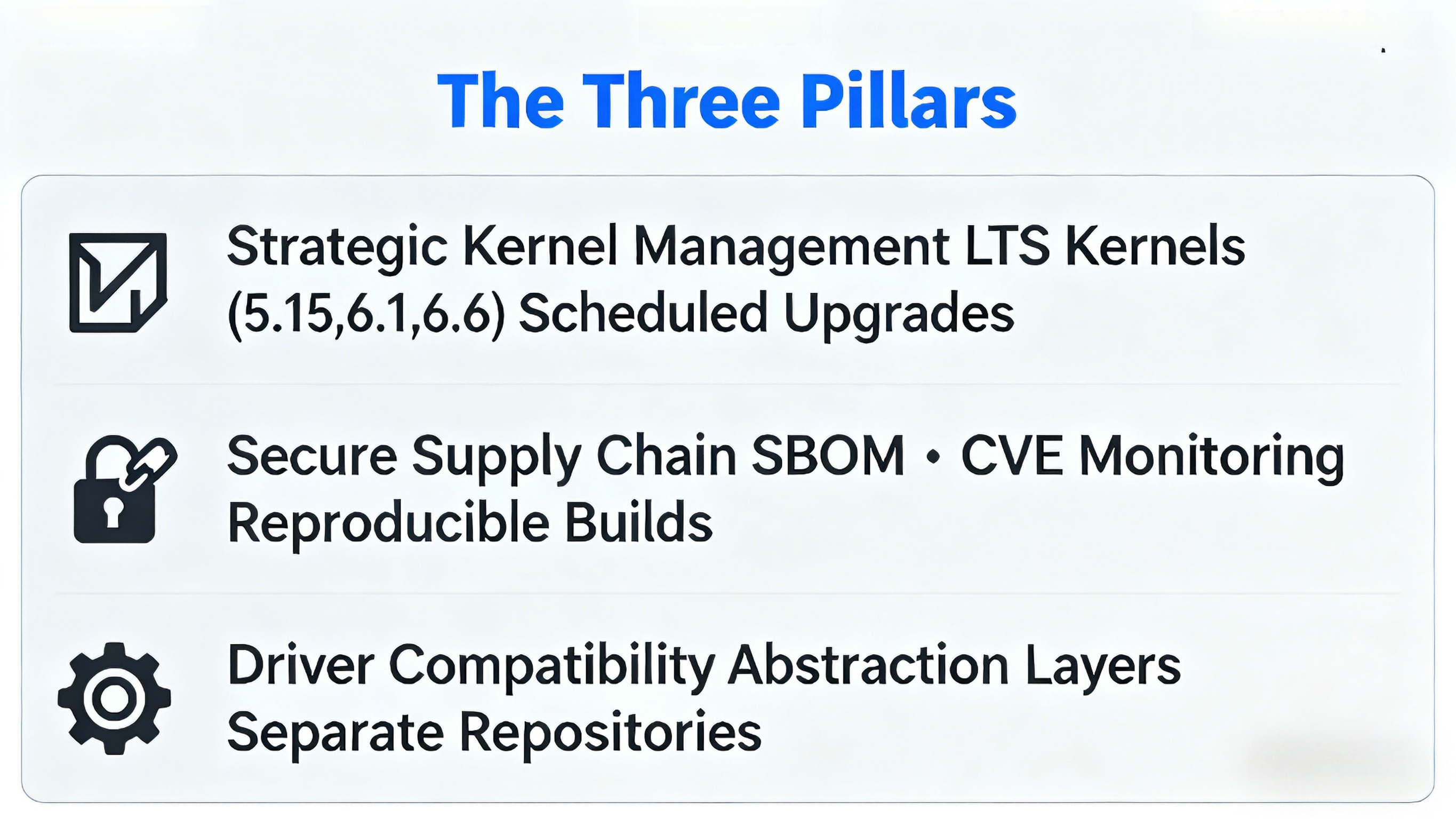
2. Secure Software Supply Chain: Knowing Your Dependencies
Modern embedded systems average 500+ software dependencies. Tracking these is non-negotiable.
Essential Practices:
Maintain a Software Bill of Materials (SBOM) for every build
Automate CVE monitoring for all components
Implement reproducible builds to ensure consistency
Use cryptographic signing for all firmware updates
"We found 23 vulnerable libraries in our codebase through automated SBOM analysis. Manual review would have taken weeks." — Embedded Team Lead, Industrial IoT Company
3. Driver Compatibility & Maintenance: The Silent Killer
Hardware changes, but your software must adapt. Driver maintenance is where most long-term projects fail.
Proactive Strategies:
Maintain abstraction layers between drivers and application code
Keep custom drivers in a separate repository from main kernel sources
Validate driver compatibility with each kernel update
Document hardware dependencies for every driver

Building a Sustainable Maintenance Framework
The "Maintenance MVP" Approach
You don't need a massive team, but you do need the right processes:
Monthly Security Review: 2 hours to scan and assess new vulnerabilities
Quarterly Compatibility Check: Validate against upcoming kernel changes
Annual Major Version Assessment: Plan for significant upgrades
Automation: Your Force Multiplier
Implement CI/CD pipelines that build and test against multiple kernel versions
Use automated testing on actual hardware, not just emulators
Create automated alerts for end-of-life announcements in your stack
The Business Case: Beyond Technical Debt
The cost of neglect isn't just technical—it's business-critical:
A single security breach can destroy brand reputation built over decades
Emergency certification recertification costs 3-5x planned updates
Customer trust erosion when devices become insecure prematurely
One automotive supplier learned this hard way: a $2M recall because they couldn't update 10-year-old infotainment systems facing new threats.
Your Action Plan for the Next Decade
Start Today: Document your current software bill of materials
Choose Your Foundation: Commit to an LTS kernel with 4+ years of support remaining
Build Your Process: Implement monthly security reviews and annual upgrade planning
Automate Vigilance: Set up automated CVE monitoring and compatibility testing
The companies that thrive in embedded aren't those with the most advanced hardware—they're the ones whose software still runs securely a decade from now.
How are you tackling software longevity in your embedded projects? Share your experiences in the comments below.
Contact: Tom
Phone: +86 18933248858
E-mail: tom@angxunmb.com
Whatsapp:+86 18933248858
Add: Floor 301 401 501, Building 3, Huaguan Industrial Park,No. 63, Zhangqi Road, Guixiang Community, Guanlan Street,Shenzhen,Guangdong,China
We chat
